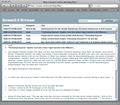
Screen2.0
hints & tips // 2011.04.26 08:44:43 [hh]
"iPhone"-Sicherheitslücke: gesamtes Bewegungsprofil auf Karten anzeigen
Das "iPhone" speichert alle Bewegungen. Eine kleine kostenlose Open-Source-App namens "iPhoneTracker" kann diese Daten sichtbar machen. Dieses "Feature" ist eine klare Lücke im Datenschutz, weil die Daten offenbar auch die komplette Neuinstallation überleben. Besonders interessant ist zum Beispiel die Frage, wo das Phone vor dem eigenen Besitz war.
Fragen und Antworten zu "iPhoneTracker" (englisch)
How does the application work?
If you run it on an OS X machine that you’ve been syncing with an iPhone or an iPad with cellular plan, it will scan through the backup files that are automatically made, looking for the hidden file containing your location. If it finds this file, it will then display the location history on the map.
How can I examine the data without running the application?
It will be stored in a folder inside /Users/
The Manifest.mbdb and Manifest.mbdx files contain a listing of the real names of the files represented by random strings in that folder. Luckily, Alasdair found a Python script here that can convert those:
http://stackoverflow.com/questions/3085153/how-to-parse-the-manifest-mbdb-file-in-an-ios-4-0-itunes-backup
If you cd into the folder in the terminal, and run iphonels.py you'll see a listing of all the files with their real names. Now, pipe it through grep to find the file we want, eg:
~/Downloads/iphonels.py | grep "consolidated"
You should see something like this:
-rw-r--r-- 00000000 00000000 28082176 1297319654 1297319654 1282888290 (4096c9ec676f2847dc283405900e284a7c815836)RootDomain::Library/Caches/locationd/consolidated.db
That text in brackets just before 'RootDomain::' is the name of the actual file on disk that holds the location data. Since it's an SQLite database file, you can use any standard SQLite browser, I'm using this Firefox plugin:
https://addons.mozilla.org/en-US/firefox/addon/sqlite-manager/
Open up the file, choose the 'CellLocation' table, and you can browse the tens of thousands of points that it has collected. The most interesting data is the latitude, longitude location and the timestamp. The timestamp shows the time in seconds since January 1st 2001.
Does this application share the information with anyone?
No. All the data stays on your machine. The code behind it has been open-sourced so you can inspect the code and compile it yourself if you’re a developer.
What can I do to remove this data?
This database of your locations is stored on your iPhone as well as in any of the automatic backups that are made when you sync it with iTunes. One thing that will help is choosing encrypted backups, since that will prevent other users or programs on your machine from viewing the data, but there will still be a copy on your device.
Why is Apple collecting this information?
It’s unclear. One guess might be that they have new features in mind that require a history of your location, but that’s pure speculation. The fact that it's transferred across devices when you restore or migrate is evidence the data-gathering isn't accidental.
Is Apple storing this information elsewhere?
There’s no evidence that it’s being transmitted beyond your device and any machines you sync it with.
What’s so bad about this?
The most immediate problem is that this data is stored in an easily-readable form on your machine. Any other program you run or user with access to your machine can look through it.
The more fundamental problem is that Apple are collecting this information at all. Cell-phone providers collect similar data almost inevitably as part of their operations, but it’s kept behind their firewall. It normally requires a court order to gain access to it, whereas this is available to anyone who can get their hands on your phone or computer.
By passively logging your location without your permission, Apple have made it possible for anyone from a jealous spouse to a private investigator to get a detailed picture of your movements.
Why did you open-source this code, won’t that make the problem worse?
We did hesitate over the right thing to do in this case, but when it became clear that "Individuals familiar with iPhone forensic analysis will be quite familiar" with it, as Ryan Neal puts it and that at least one other person had tried to alert the public but apparently failed to make it clear what was going on, a demonstration application seemed the lesser evil.
To make it less useful for snoops, the spatial and temporal accuracy of the data has been artificially reduced. You can only animate week-by-week even though the data is timed to the second, and if you zoom in you’ll see the points are constrained to a grid, so your exact location is not revealed. The underlying database has no such constraints, unfortunately.
Why are some points in places I’ve never visited?
As far as we can tell, the location is determined by triangulating against the nearest cell-phone towers. This isn’t as accurate as GPS, but presumably takes less power. In some cases it can get very confused and temporarily think you’re several miles from your actual location, but these tend to be intermittent glitches.
How was it discovered? We’ve been collaborating on several location data visualization projects, for example this map of radiation levels in Japan: http://www.guardian.co.uk/science/blog/2011/mar/24/fukushima-radiation-levels
We’d been discussing doing a visualization of mobile data, and while he was researching into what was available, Alasdair discovered this file. At first we weren’t sure how much data was there, but after we dug further and visualized the extracted data, it became clear that there was a scary amount of detail on our movements. It also became obvious that at least some other people knew about it, but it wasn't being publicized.
What’s your relationship with Apple?
Pete worked for Apple for five years, and left three years ago on good terms. He had no contact with anything iPhone related, (he worked on desktop visualization software) and received no help or information from inside the company while researching this problem. We’re both big fans of Apple’s products, and take no pleasure in uncovering this issue.
You say no data is shared, but why do I see the web accessed when I run the app?
The visualization is implemented as a view onto a local web page using the OpenHeatMap jQuery plugin. This means that the following resources are pulled from the web:
All of these are just static files that are downloaded from the web, and none of your data ever leaves your machine. We do still recommend inspecting the source code if you're a developer, or even just relying on the directions that allow you to inspect the data using standard database tools.
Direkter Link: petewarden.github.com/ iPhoneTracker
Werbung